advanced persistent threat appropriate
Usually associated with nation-state actors, Advanced Consistent Threat (APT) is really a type of cyberattack. Anxinsec calls for sophisticated and even complex hacking strategies. Typically, APT episodes use multiple strike vectors, and usually are designed to avoid detection and grab information.
In some sort of typical APT strike, a group of cybercriminals infiltrates an organization's networking. The goal is usually to steal very sensitive information. In order to do this, the opponents will use many different methods including sociable engineering, network invasion, and malware. Additionally they frequently attempt to generate a backdoor throughout the target's system. This allows the attacker to gain access to the system at any time.
The primary objective of the advanced persistent threat is to take valuable information, usually from companies or perhaps government organizations. On the other hand, there are numerous other motives. APTs can also disrupt the functions of the concentrate on and steal sensitive information about high-level personnel.
APTs are usually usually performed by simply well-funded, experienced clubs of cybercriminals. That they may evade diagnosis for months or years. In reality, Stuxnet, a 500 kilobyte computer worm, was considered to have been in development for nearly a ten years before it had been found out in 2010.
An Advanced Persistent Threat is definitely an organized, strategic, and complex cyberattack. It is sometimes a for-profit, state-sponsored attack. However, it can also be a politically encouraged attack.
advanced persistent threat security
Integrated Advanced Continual Threat Protection Options are designed in order to safeguard businesses in opposition to persistent malicious assaults. These solutions may well include sandboxing, forensic analysis, reputation networks, EDR, and CASB. These solutions may be integrated into application, virtual appliances, or perhaps physical appliances.
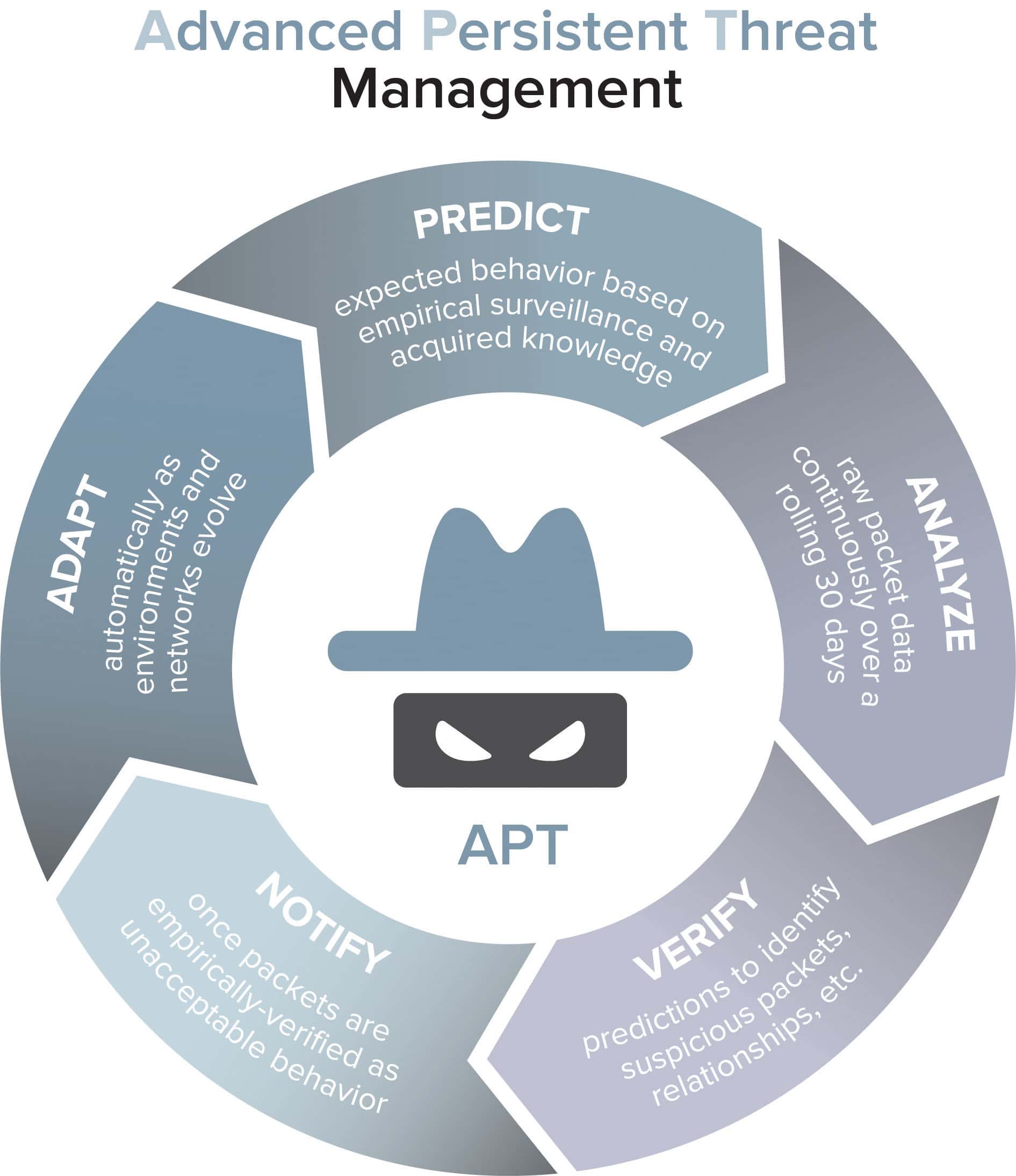
Advancements in technology are really accelerating the necessity for advanced APT protection solutions. Leading security vendors are developing innovative products in order to support companies all the way through this difficult pandemic. These innovations consist of deep learning strategies that were used by Cornell University or college to identify a good APT attack earlier.
APT protection options are expected to be able to witness an evident growth in typically the coming years, influenced by increasing cybercrimes and stringent authorities regulations towards adoption of APT protection policies. Industry is furthermore expected to expand due to typically the proliferation of cloud based APT security solutions. Nevertheless , growing cyber-security costs may be a key factor limiting typically the growth of the promote.
Companies are in search of advanced defenses to safeguard their databases and networks. Anxinsec can be deployed in virtual kitchen appliances, private clouds, or physical appliances.
The global Advanced Consistent Threat Protection Market was valued at USD 5. a couple of billion in 2020 and is estimated to succeed in USD 13. 6 billion by 2025. The industry is segmented into Deployment Mode, End User, Services, and Region. The Asian countries Pacific sub-segment is usually expected to witness the fastest progress throughout the forecast time period.
advanced persistent threat defense
Protecting against Advanced Consistent Threats can end up being a tough problem. These threats are really difficult to identify and will remain unknown for years. They often exploit multiple disadvantages and use deliberate decoys to mislead defenders.
APT attacks have become more widespread over the prior few years. These kinds of attacks use thoroughly planned techniques in order to steal sensitive data and systems. Generally, these attacks target high-profile organizations and governments.
APT attacks are usually carried out by hostile express institutions, governmental businesses, and other groupings connected to nation-states. That they use a multi-phased attack on a business' network. These disorders are expensive in addition to take an extended time to discover. A successful assault can have damaging consequences.
Advanced Persistent Threats are recognized to steal data and can degrade system capability. Effective attacks can end result in regulatory charges, civil unrest, and consumer lawsuits.
Breakthroughs in technology are expected to increase the necessity for incorporated security solutions. Foriegn adoption will likewise drive the GOOD security market. At the moment, most companies focus on blocking specific viruses threats.
An APPROPRIATE attack is the multi-stage attack of which typically targets high-value targets. It might last months or years, depending on the menace. The goal involving a trigger is usually to gain entry right into a network and become a shadow government team.








